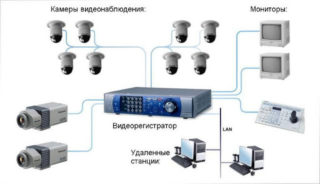
The security system in the house or on the site can be organized in various ways. The video surveillance scheme depends on the nature of the cameras and recording devices used. Today, a system based on IP devices is the most efficient.
Main components
Necessary elements of the system:
- IP cameras - the device captures the image and compresses the signal in the format that is used to transmit data on the Internet - the TCP / IP protocol. The video image in this form can be directly transmitted via an available Internet connection to a computer, digital video recorder, mobile phone.
- Server - a system control unit. It requests an image, transfers data, records and saves. The server can run as an application on stand-alone hardware or in a virtual environment.
- Cables - system components are connected using twisted pair or Ethernet cables.
- Software - free or commercial software. The software provides tools for monitoring and recording. Paid software gives you more options: unlimited archive for storage, integration with other subsystems, number recognition and more.
A standard web browser allows you to view images from cameras. However, to manage multiple devices, you should install special software.
Block diagram of video surveillance
The IP video surveillance scheme is built in compliance with certain principles. There are 2 approaches:
- The network is segmented. Each local sector is associated with an access point to the Internet or storage.
- With the access of each computer to each video device structure.
2 schemes are more common: direct and cross. The first is based on segmentation. The structure resembles a star: in the center is the main device for storing or processing data, and according to the "rays" - the camera.
Straight
A simplified connection diagram for a video surveillance system looks like this:
- 1 or more cameras are connected to the switch.
- Access to the video stream from the cameras of this segment is given to a computer connected to their common node device.
- Surveillance data for a user from another zone remains inaccessible.
The user can view data only when connected to the server. In such a structure, access rights are easily regulated.
Cross
The scheme of the video surveillance system provides access to data from cameras to all participants, wherever they are. The signal from the IP device is routed to any network node. The cross model should use modern models with an internal authorization system. They can be members of a local and global network.
The scheme is simple, since there is no exact sequence here, the connection is subject to the requirements of security or convenience. But regulating user access to this data is difficult. Rebuilding such a structure is also difficult, since the connections in it are entangled.
Methods of video surveillance
There are many ways to organize video surveillance with remote access: from the simplest, based on 1 camera, to complex multi-component systems. The average user is usually faced with simple schemes.
With one IP camera
Such a system can hardly be called complete. But if the goal is to monitor the situation at home, that's enough.
Any IP camera is a standalone network device capable of transmitting data stream to any other user device.Where it is located - in a local or external network - does not matter, it is important here to draw up the route correctly.
Need to get a static IP address. By default, the provider provides the device with a dynamic address to which the data packet cannot be transmitted. When the static address is received, the camera is connected to the PC using a cable and the received address is entered into the browser. Then indicate the port for the camera - usually 80, and set the username and password that the user will use.
The camera is disconnected from the PC and the provider's cable is connected to it. Now data from the recorder is available.
Remote video surveillance using a router
If the structure includes several cameras, it is more profitable to use a network router. Cameras, a router, and other devices form their own subnet. Access is performed by transferring the request from the Internet to the local network.
The order is as follows: the user needs to get a static IP address, assign a forwarding port to each camera in the router interface. Then you need to connect the cameras directly and assign a local ip address to each one.
They also set up Wi-Fi cameras.
DVR Introduction
The DVR allows you to create an extensive archive of recordings. The user can observe in live mode and view the captured frames. The scheme for constructing an IP video surveillance system is more complicated. It is necessary to obtain a static IP address for the router and for the DVR and associate it with the MAC address. Otherwise, the router may assign another, and the transfer will become impossible.
The address of the DVR is indicated in the router. A request is transferred from the router to the registrar. Then, forwarding to the port of each camera is executed on the DVR and their local addresses are registered.
The request to the registrar from the local network is carried out at the local address, and not global. It is impossible to do this from the inside. To check external access, use another device with access to the global network.
Using Cloud Services
Obtaining a static IP address is increasingly becoming a paid service. The organization of cloud surveillance allows you to get around this difficulty. The DVR is constantly connected to the cloud, the user can access observations through any device if he calls the correct password and login. The need for settings and getting a static address disappears.
The disadvantage of the structure is the low connection speed. However, for those who use mobile devices, it does not matter for viewing, since here the speed is initially limited by the 3G standard.
Equipment Selection Criteria
The construction of a video surveillance system includes one more requirement - profitability. To maintain a balance between reliability and cost, consider:
- Access to the database if you plan to store a large amount of data. All other advantages - easy access, simple operation, it does not matter.
- Resizing - reducing the size allows you to increase the size of the archive. But so that viewing later does not cause difficulties, you need to use a scheme that allows you to resize when viewing.
- Free access to the surveillance camera is a prerequisite.
- Security - access to structure elements is password protected. The IP camera encrypts the signal before it is transmitted to the recorder.
- Creating an archive - if transferring to the archive is difficult, the system is worthless.
You also need to pay attention to the options. For example, the analytics option is useful to the store owner, and the ability to mark frames and frame-by-frame playback is useful to the security guard.
CCTV Benefits
 The security and surveillance system based on IP cameras has the following advantages:
The security and surveillance system based on IP cameras has the following advantages:
- Cameras compress the video signal. The received digital packet can be directly transmitted to the network or to any digital device.
- Security - data is encrypted before being transferred to a DVR or router. Access to the archive is possible only by entering the correct username and password.
- The system can be built according to various schemes, taking into account the number of cameras, the method of transmitting data storage, and the need for free access.
- The owner can view data from any device, including from his own smartphone. The distance is not important.
Disadvantages:
- The quality of shooting, bandwidth, ease of management depend on the equipment used and the selected scheme.
- The speed of receiving data from storage is limited by the channel width.
- It is necessary to update the software periodically so that the system remains operational.
The video surveillance organization scheme is selected taking into account the number of cameras, the purpose of observation, the storage method and other factors. If difficulties arise, it is best to consult a specialist.